Access control is a crucial aspect of information security that regulates who or what can view or use resources in a computing environment. It serves as a protective barrier to ensure that sensitive information is only accessible to authorized individuals or systems. In this article, we will delve into the basics of access control, explore its necessity, and discuss three major types: Role-Based Access Control (RBAC), Attribute-Based Access Control (ABAC), and Policy-Based Access Control (PBAC).
What is Access Control?

Table of Contents
Access control is the process of managing and restricting access to specific resources or areas within a system. It involves defining rules and policies to govern who can access what, under what conditions, and for how long. This practice safeguards sensitive data, prevents unauthorized use, and contributes to overall system security.
Why We Need Access Control?
Access control is essential for several reasons:
- Data Protection: It ensures that confidential information is only accessible to those with proper authorization, reducing the risk of data breaches.
- Compliance: Many industries must comply with regulations that mandate strict access controls to protect sensitive information and maintain privacy.
- Preventing Unauthorized Use: It helps prevent unauthorized users or systems from accessing resources, minimizing the potential for malicious activities.
Types of Access Control
There are three major types of access control.RBAC, ABAC, and PBAC.In this article, we will get a high-level idea of each type of access control mechanism, and where it can be used.
Role-Based Access Control (RBAC)
Role-based access control (RBAC) assigns permissions based on predefined roles, streamlining the management of access rights.

This access control mechanism is widely used in organizations with hierarchical structures where job roles determine access levels.
For example let’s say in an organization there are multiple roles such as HR, ACCOUNTANT, and EMPLOYEE. Based on these roles they will have access to Company data, or do certain things. Users with HR roles will have access to all employees’ data and can approve leaves, Users with FINANCE-ADMIN roles can only see company financial data. Users with EMPLOYEE roles can view their own data and salary, and apply for leave.
Attribute-Based Access Control (ABAC)
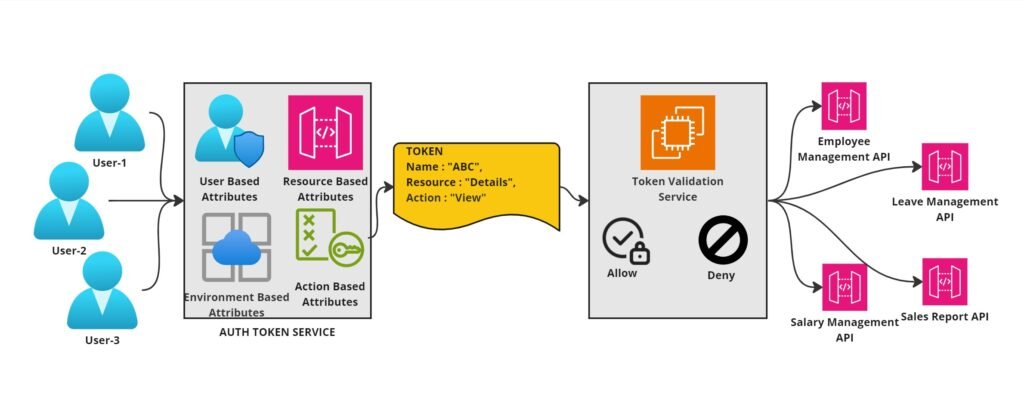
Attribute-Based Access Control (ABAC) is a way of deciding who gets access to what in the system. Instead of focusing on job roles like manager or employee, ABAC looks at specific characteristics, or attributes, of the users and the resources they want to access. The main goal of ABAC is to make sure that only the right people, with the right characteristics, can access certain things, like data or computer systems. It’s like a security guard checking if someone has the right ID before letting them into a restricted area. With ABAC, an organization’s access policies enforce access decisions based on the attributes of the subject/Users, Resource, Action, and Environment involved in an access event.
The user requests access, with attributes like ID, job roles, group memberships, and security clearance. ABAC systems get this data from HR systems or during log-in.
The Resources or objects the user wants to access, such as a file, application, server, or API. Resource attributes include creation date, owner, file name, type, and data sensitivity.
Actions: What the user is trying to do with the resource, like “read,” “write,” “edit,” “copy,” or “delete.” In some cases, multiple attributes can describe an action.
Environment: The broader context of each access request, including time, location, subject’s device, communication protocol, encryption strength, and risk signals like authentication strength and normal behavior patterns.
Policy-Based Access Control (PBAC)
Policy-Based Access Control (PBAC) is a sophisticated approach to managing access within a computer system or network. In PBAC, access decisions are driven by predefined policies rather than relying on fixed roles or user attributes. These policies specify the conditions under which access is granted or denied, providing a high degree of flexibility and granularity in access control. PBAC enables organizations to tailor access rules based on specific scenarios, allowing for a more nuanced and adaptive security framework. This method is particularly advantageous in complex environments where diverse users interact with a variety of resources. While PBAC offers unparalleled customization, careful policy definition is crucial to avoid unintended consequences or overly complex access structures. Organizations often implement PBAC to ensure that access control aligns with their unique operational needs, offering a dynamic and responsive solution to evolving security challenges.
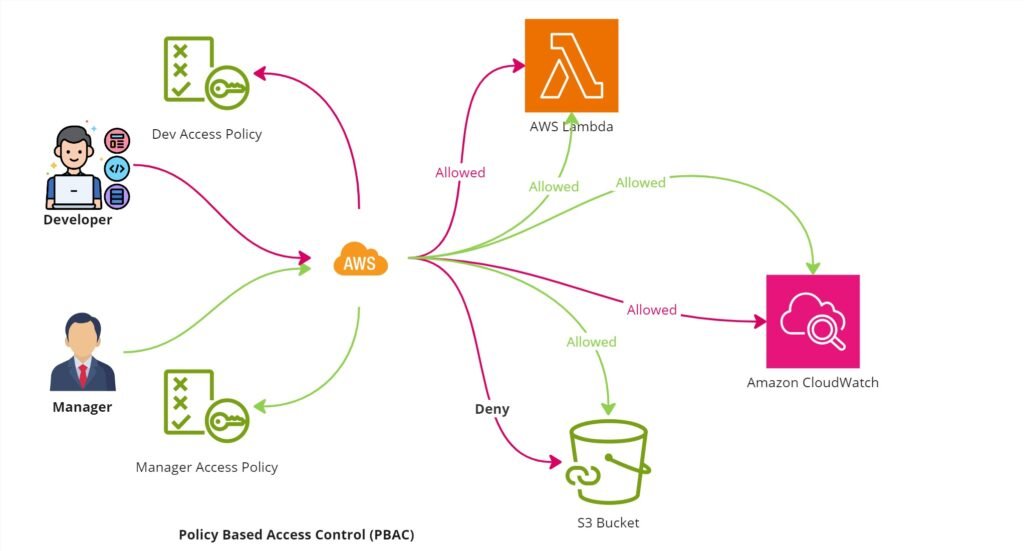
For Example, let’s say in the AWS Account, we’ve implemented Policy-Based Access Control (PBAC) with two IAM roles: “Developer_Access_Role” and “Manager_Access_Role.” The “Developer_Access_Role” is associated with “Developer_Access_Policy,” granting basic development permissions like ListFunctions and InvokeFunction. The “Manager_Access_Role” inherits these and adds managerial capabilities, including S3 PutObject and S3 DeleteObject. Users are assigned roles based on their responsibilities. During login, access control checks users’ roles and policies. This ensures developers have essential permissions, while managers enjoy extended access. This PBAC model enhances security, aligns with the principle of least privilege, and streamlines resource management.
Conclusion
In conclusion, understanding the different types of access control is fundamental to implementing effective security measures. Whether using RBAC for simplicity, ABAC for flexibility, or PBAC for granular control, organizations must tailor their approach to meet specific needs. A well-designed access control strategy not only protects sensitive data but also contributes to overall system integrity and compliance with regulatory requirements.
