Table of Contents
In today’s interconnected world, ensuring application security testing is paramount. With cyber threats evolving at an alarming rate, organizations must prioritize building robust application security testing programs to safeguard their systems and protect sensitive data. In this guide, we’ll explore the essential steps involved in creating an effective application security testing program that enhances the security posture of your applications.
Understanding the Importance of Application Security Testing
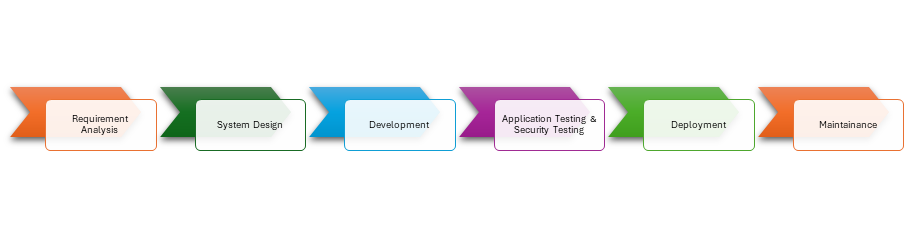
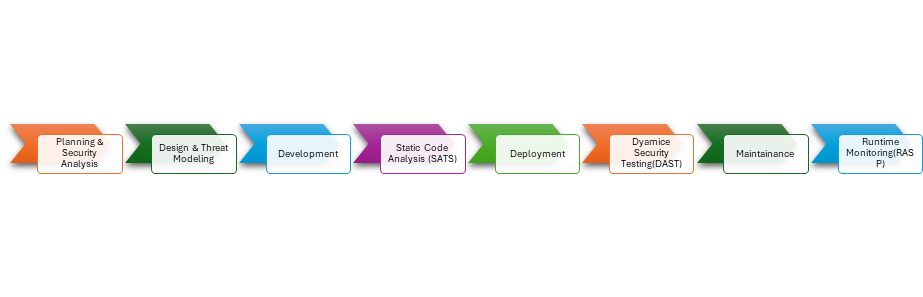
The importance of application security testing cannot be overstated. It helps identify and mitigate vulnerabilities in software applications before they can be exploited by malicious actors. By proactively conducting security testing, organizations can minimize the risk of data breaches, financial losses, and reputational damage.
Types of Application Security Testing: Choosing the Right Approach
Before diving into building a security testing program, it’s essential to understand the different types of security testing available:
- Static Application Security Testing (SAST): Analyses source code or binary files to identify potential security vulnerabilities.
- Dynamic Application Security Testing (DAST): Evaluates running applications for vulnerabilities by simulating attacks.
- Interactive Application Security Testing (IAST): Combines elements of SAST and DAST, offering real-time feedback during application runtime.
- Runtime Application Self-Protection (RASP): Provides security monitoring and protection within the application runtime environment.
Each type of testing offers unique advantages and should be selected based on the specific requirements and constraints of your organization.
Planning Your Security Testing Program: Setting the Foundation
A successful security testing program begins with careful planning:
- Identify Assets and Threats: Determine the critical assets to protect and the potential threats they face.
- Define Testing Objectives and Scope: Clearly outline the goals and scope of your security testing efforts to ensure alignment with organizational priorities.
- Select Appropriate Tools and Techniques: Choose security testing tools and techniques that best fit your organization’s needs and technology stack.
- Allocate Resources and Establish Timelines: Ensure adequate resources are allocated for testing activities and establish realistic timelines for implementation.
Integrating Security Testing into the SDLC: Making Security Everyone’s Responsibility
Integrating security testing seamlessly into the Software Development Lifecycle (SDLC) is crucial for ensuring the effectiveness of your program:
- Incorporate Testing at Each Stage: Integrate security testing activities into every stage of the SDLC, from requirements gathering to maintenance.
- Empower Developers: Provide developers with the tools, training, and resources they need to conduct secure coding practices and identify vulnerabilities early in the development process.
- Automate Where Possible: Implement automation to streamline security testing processes and minimize manual effort.
Conducting Security Testing: Putting Theory into Practice
Executing security testing requires careful execution and analysis:
- Configure Testing Environments: Set up testing environments that accurately mirror production environments to ensure realistic results.
- Run Tests Using Selected Tools and Techniques: Execute security tests using chosen tools and techniques, following predefined testing objectives and scope.
- Analyse Test Results: Thoroughly analyze test results to identify and prioritize vulnerabilities based on severity and potential impact.
- Remediate Identified Issues: Take prompt action to remediate identified vulnerabilities, working closely with development and operations teams to implement fixes.
Establishing Testing Metrics and Reporting: Demonstrating Effectiveness
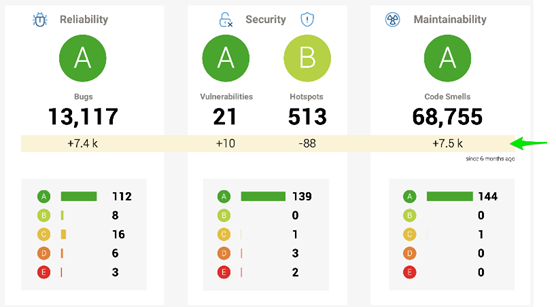
Measuring the effectiveness of your security testing program is essential:
- Define Key Metrics: Establish key performance indicators (KPIs) to measure the success of your security testing efforts, such as the number of vulnerabilities detected, time to remediation, and overall security posture improvement.
- Generate Comprehensive Reports: Create detailed reports summarizing test results, including identified vulnerabilities, their severity levels, and recommended remediation actions.
- Communicate Findings to Stakeholders: Share reports with relevant stakeholders, including developers, managers, and executives, to raise awareness of security issues and demonstrate the value of the security testing program.
Continuous Improvement and Adaptation: Evolving with the Threat Landscape
Security is an ongoing journey that requires continuous improvement and adaptation:
- Stay Informed About Emerging Threats: Keep abreast of emerging security threats, vulnerabilities, and best practices to adapt your security testing program accordingly.
- Regularly Review and Refine: Conduct regular reviews of your security testing program to identify areas for improvement and refine processes and procedures as needed.
Encourage Collaboration and Knowledge Sharing: Foster a culture of collaboration and knowledge sharing among security, development, and operations teams to strengthen the overall security posture of your organization.
Conclusion
Building an effective application security testing program is essential for protecting your organization’s applications and mitigating the ever-present threat of cyber attacks. By following the steps outlined in this guide and adopting a proactive approach to security testing, you can enhance the security posture of your applications and safeguard your organization’s valuable assets and reputation in today’s rapidly evolving threat landscape. Remember, security is not a one-time effort but an ongoing commitment to staying one step ahead of cyber threats and building a more secure future for all.

This article emphasizes the critical role of application security testing in safeguarding against cyber threats. It outlines the importance of understanding different types of security testing, including SAST, DAST, IAST, and RASP, and the necessity of integrating security testing into the SDLC. The guide also highlights the importance of planning, executing, and measuring the effectiveness of security testing programs, and the ongoing need for continuous improvement and adaptation to emerging threats.
Great article.